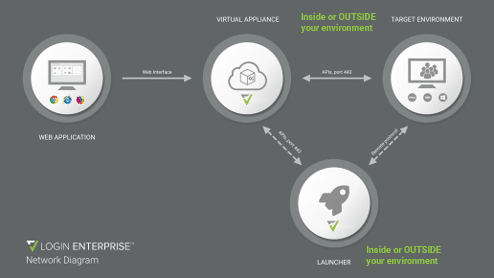
The Intersection of Security and User Experience
December 12, 2022
Most IT organizations struggle to balance end-user resistance and the need for change. Although implementing change bolsters defense against advanced security threats, many IT teams face troubles managing internal user resistance.
So how can IT support changing security requirements while maintaining a positive end-user experience? To effectively manage this circumstance, start with these critical considerations.
How Driving Security Forward Can Impact the Organization
Before deploying a change, consider the following:
- Can end users do their jobs as well as or better than before the change was implemented?
- Is the post-change outcome predictable?
- How can the organization’s attack surface be reduced?
- Will the change create a “grey market”? Will end users begin looking outside company-authorized tools to get their job done?
Balancing User Experience and Identity Management
The use of multi-factor authentication devices has increased significantly in the last ten years—enabling end-users to access systems while adding a layer of protection beyond password-only.
However, bypassing testing modifications at the identity provider level before live implementation can open your organization up to a significant outage.
Any change at that level can lock end users out of the systems they need to perform their jobs, halting business continuity and stopping users in their tracks.
So how can you avoid this type of outage? The best practice would be to include your identity provider as part of regular testing parameters. By doing so, you can ensure that your security posturing does not impact the users’ ability to access critical systems.
Understanding Capacity and User Experience
Across industries, companies are looking to adopt practices that ensure user experience does not diminish as capacity rises. But overcoming barriers to optimizing user experience starts with assessing the limits of your current architecture.
Consider this: how many users can your current architecture support, and do your existing resources properly support your users?
If you have any uncertainty about these questions, take some time to outline the resources needed to support your users.
For example, our Solutions Architect, Paul Morrissey, saw the impacts of this occurrence play once in real-time. In his experience working with a large financial institution, he recalls an instance when he asked his team how many users their current configuration could support. After finding out that there was no clear answer to this question– a lightbulb moment went off for him.
The organization could not accurately anticipate disruptions because there was no clear way of understanding at what point capacity would lead to a breaking point.
Like many organizations, this reactive approach does not support user experience because it only evaluates capacity when systems begin to fail.
Implementing security enhancements without the proper considerations can consume much more resources than anticipated, resulting in unplanned expenditures and reducing funds budgeted for other improvements.
Managing Predictable Outcomes
Another challenge that delays security modifications is the inability to determine the outcome of an update until after deployment. Quantifying the impact of change before your end users are exposed can help you avoid negative performance impacts on your existing user base.
Waiting to observe negative performance impacts on your existing user base absorbs resources. Investing in a monitoring solution is a proactive way to understand how an update or change impacts end users.
The management interfaces of some monitoring solutions can add overhead, as they sit within the systems, providing resources for the same end users you are attempting to monitor.
It would be best to account for this in your production environment and limit what is running to offer the best user experience.
Leave Your Antivirus Software Running
There is a risk in implementing systems that counteract your security posture. These types of systems consume a disproportionate number of resources that support the user base—which is a problem that scales proportionally based on the size of an organization.
Consider implementing solutions that don’t disarm or offset your security posture as part of your testing parameter. By leaving your security software enabled, you can gain benefits like the ability to:
- Verify that your workflow is functional while being secure.
- Eliminate surprise overhead by determining resources before production.
- Budget for the cost of updating.
Learn more about managing the delicate balance between security and user experience in our on-demand presentation, Closing the Gap Between Advancing Security and Employee Experience.